Tracehunters Team
Welcome to Tracehunters: The Future of OSINT Investigations
Open Source Intelligence (OSINT) investigations have never been easier or more powerful. Tracehunters provides a revolutionary visual platform that transforms complex investigations into intuitive, connected workflows. Whether you're a seasoned investigator, journalist, security researcher, or someone just getting started with OSINT, this guide will walk you through everything you need to know.
Creating Your Account: Simple Yet Secure
Getting started with Tracehunters is straightforward and designed with security in mind. Here's how the registration process works:
Step 1: Registration
- Visit the registration page - Click "Get Started" from the homepage or navigate directly to
/register - Fill in your details:
- Full Name: Your real name for account verification
- Email Address: This will be your login credential and where verification emails are sent
- Password: Create a strong password (the system includes validation to ensure security)
- Confirm Password: Re-enter your password to prevent typos
- Accept Terms: Agree to Tracehunters' terms and conditions
- Submit: Click "Create Account"
Step 2: Email Verification
After registration, you'll receive two important emails:
- Verification Email: Contains a link to verify your email address - this step is mandatory
- Welcome Email: Includes helpful getting-started information
Step 3: Account Activation
Click the verification link in your email to activate your account. Once verified, you can log in and start building investigations.
Understanding Your Dashboard
Once logged in, you'll land on your Investigations Dashboard (/workflows). This is your mission control center where you can:
Personal Investigations
- View all your private investigations
- Create new investigations (free users get 1, paid users get unlimited)
- See creation dates and descriptions
- Access investigation settings
Team Investigations (Pro Feature)
- Collaborate with team members on shared investigations
- View team-specific investigations
- Manage team permissions and access
Investigation Management
Each investigation card shows:
- Investigation name and description
- Privacy settings (Public or Private)
- Creation date
- Quick access to view and edit
Building Your First Investigation
The heart of Tracehunters is the Visual Workflow Builder - a drag-and-drop interface that lets you map relationships between entities.
The Entity Library
Tracehunters provides 14 different entity types for comprehensive investigations:
Core Entities:
- Person: Individual subjects with properties like name, role, email, phone
- Organization: Companies or groups with name, type, website
- Location: Physical places with address, city, country details
Digital Entities:
- Website: Web presence with URL and category
- Account: Social media/online accounts with platform, username, URL
- Email: Email communications for tracking correspondence
- IP Address: Network identifiers for technical investigations
Evidence & Documentation:
- Document: Files and documents relevant to the investigation
- Evidence: Proof or findings with detailed properties
- Event: Incidents or happenings with timestamps
Financial & Assets:
- Crypto Wallet: Cryptocurrency addresses for blockchain investigations
- Bank Account: Financial institution details
- Vehicle: Transportation assets for physical investigations
Relationships:
- Connection: Custom relationships between any entities
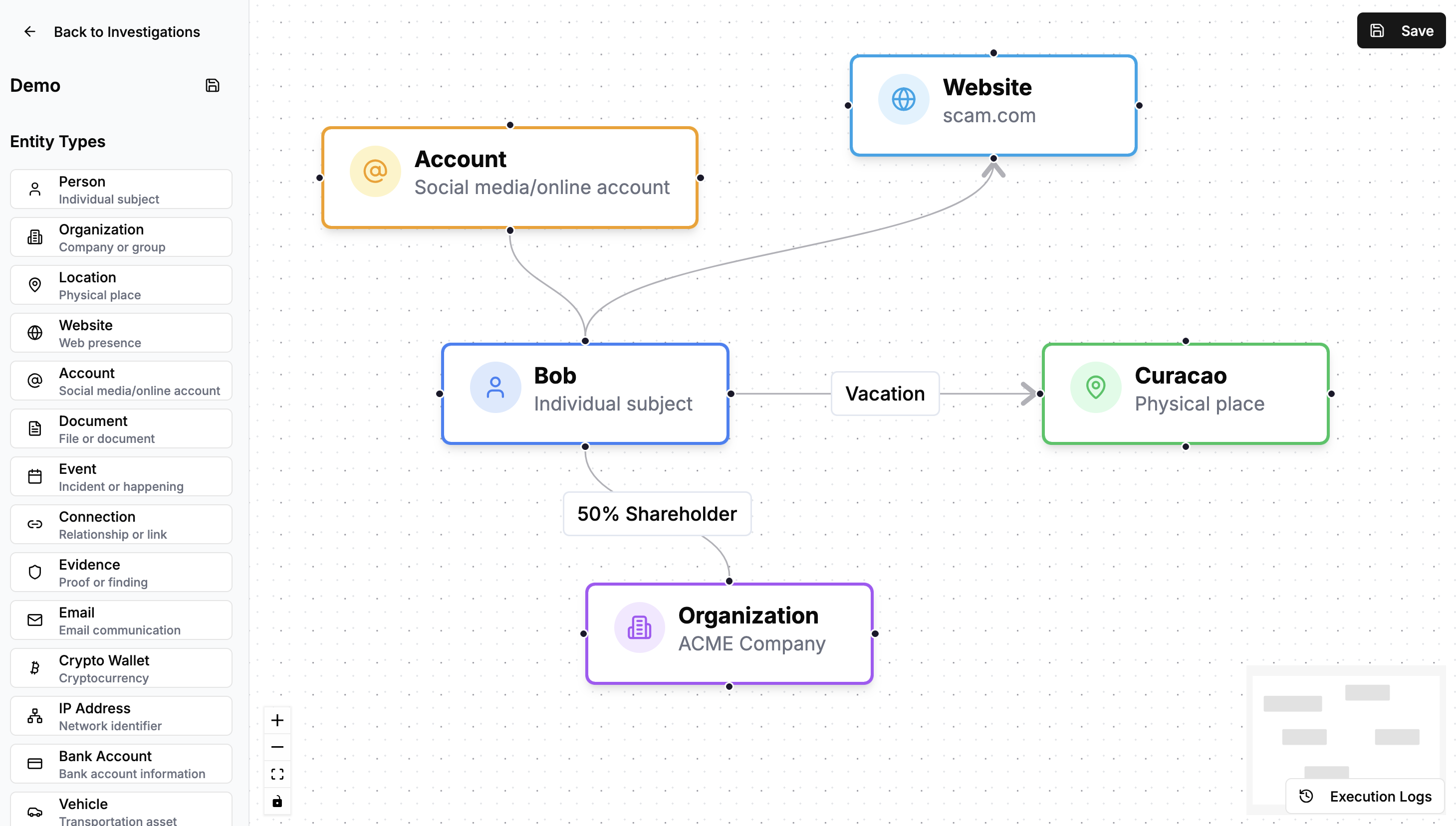
Creating Your Investigation Map
- Drag entities from the sidebar onto the canvas
- Configure properties by clicking on any entity to open the configuration panel
- Create connections by dragging between entities to show relationships
- Add details like names, URLs, addresses, and other relevant information
- Save your work using the save button - you can name and describe your investigation
Advanced Features
Team Collaboration (Pro):
- Share investigations with team members
- Set different permission levels
- Collaborate in real-time on complex cases
Investigation Analysis:
- Run analysis on your investigation map
- View execution logs to track investigation progress
- Generate findings and insights
Privacy Controls:
- Keep investigations private or make them public
- Control who can access your work
- Export and share findings securely
Subscription Plans: Free vs Pro
Free Plan
- 1 personal investigation - perfect for getting started
- Access to all entity types
- Basic investigation features
Pro Plan
- Unlimited investigations - scale your research
- Team collaboration - work with colleagues
- Advanced analysis features - deeper insights
- Priority support - get help when you need it
Best Practices for Effective Investigations
1. Start with Core Entities
Begin your investigation by mapping the primary subject (usually a Person or Organization) and work outward from there.
2. Use Descriptive Names
Give your investigations clear, descriptive names that you'll recognize months later.
3. Document Everything
Use the properties fields to capture all relevant information - URLs, addresses, phone numbers, dates.
4. Connect Thoughtfully
Only create connections between entities when there's a real relationship. This keeps your map clean and meaningful.
5. Save Frequently
The platform autosaves, but manually saving ensures your work is preserved with proper naming.
Real-World Use Cases
Journalist Investigations:
- Map connections between political figures and organizations
- Track financial flows and business relationships
- Document sources and evidence chains
Security Research:
- Investigate threat actors and their infrastructure
- Map attack patterns and victim relationships
- Track digital footprints across platforms
Corporate Intelligence:
- Research business relationships and partnerships
- Investigate company structures and ownership
- Map competitor landscapes
Academic Research:
- Study social networks and influence patterns
- Research organizational structures
- Document case studies and evidence